Fraud Article
Cross-border fraud: How to protect your business in 2026
Cross-border fraud is accelerating as global criminals exploit jurisdictional gaps, AI-driven tactics, and the speed of digital commerce. As online fraud continues to rise across financial services and e-commerce, international fraud is fast becoming one of the most critical risk challenges businesses face in 2026.
The rising threat of cross-border fraud
As businesses expand internationally, cross-border fraud is becoming more frequent, complex, and costly. Decision-makers in financial services are seeing an accelerating mix of sophisticated technical attacks, social engineering, and organized criminal supply chains that exploit jurisdictional gaps, uneven regulation, and the sheer velocity of digital commerce.
For global scammers, borders are optional; for most businesses, they’re still blind spots. That blunt reality explains why cross-border fraud deserves a central place in every enterprise risk and compliance agenda in 2026. International fraud isn’t an abstract risk: it directly threatens revenue, customer trust, and regulatory compliance across the U.S., the U.K., Brazil, Mexico, Colombia, and beyond. In fact, the latest Veriff report shows that about one in every 25 online identity verification attempts involves a fraudster attempting to pose as another person — a rate that remains high year-on-year and reflects how persistent and widespread international fraud attempts have become.
Explore key fraud statistics, regulatory shifts, and actionable recommendations from Veriff’s new report.
What is cross-border fraud?
Cross-border fraud refers to deceptive, unlawful activities that involve parties, infrastructure, or assets located in more than one country. That includes frauds that originate in one jurisdiction and affect victims in another, schemes that route illicit proceeds through multiple nations, and attacks that exploit international payment rails, marketplaces, or onboarding systems. Cross-border e-commerce fraud and cross-border payment fraud are prominent subtypes that impact merchants, payment processors, banks, and crypto services alike.
Key features that distinguish cross-border financial crime from domestic scams include multi-jurisdictional actors, usage of international money mules and laundering channels, and exploitation of differences in Know Your Customer (KYC) regimes and law enforcement cooperation. What’s more, fraud tactics are evolving: attacks like emulator and injection attacks — which mimic legitimate devices or insert synthetic data into identity-verification flows — are increasingly used to bypass security controls at scale.
Why are international scams increasing?
Several converging trends have driven a measurable rise in international fraud over the past five years. First, rapid growth in global digital payments and cross-border e-commerce has created more touchpoints and higher volumes of transactions that fraudsters can target. The expansion of instant, real-time payment rails and digital wallets across regions has raised both opportunity and consequence for bad actors.
Second, the professionalization of fraud ecosystems has accelerated. Organized groups now operate transnationally, offering specialized services – stolen credential lists, mule recruitment, synthetic identity kits, and layered cash-out channels – on encrypted platforms and darknet markets. These services let malicious actors scale attacks across multiple jurisdictions with low marginal cost.
Third, disparities in regulatory frameworks and enforcement capacity create uneven deterrence. Fraudsters exploit countries with lax onboarding rules, weak sanctions screening, or slow cross-border information-sharing to route funds and hide traces. Fraudsters follow the path of least resistance: weak KYC in one country, lax enforcement in another, and slow information-sharing everywhere.
Finally, the globalization of consumer identity footprints – people hold accounts, devices, and payment instruments across borders – complicates fraud detection and attribution. Remote onboarding, digital-first banking, and marketplace APIs all increase the surface area for cross-border scams while making it harder to determine jurisdictional responsibility at the time of attack.
Common types of cross-border fraud
Understanding common attack patterns is essential for prevention. The most prevalent forms of international fraud affecting businesses include:
- Cross-border payment fraud: unauthorized or fraudulent payments that traverse international rails, including card-not-present (CNP) scams, account takeovers used to initiate wire transfers, and illicit use of cross-border payout services.
- Cross-border e-commerce fraud: fake orders, stolen-card purchases, and friendly fraud where goods are shipped internationally and chargebacks are pursued from another jurisdiction to avoid detection.
- Synthetic identity fraud: creation of composite identities using fabricated and real data, often exploited to open accounts and conduct transactions across countries before detection.
- Money mule networks and layering: recruitment of individuals across jurisdictions to receive, move, and withdraw criminal proceeds, obscuring the money trail through multiple countries’ financial systems.
- Business email compromise (BEC) and invoice fraud: targeted attacks on corporate payment processes where fraudsters impersonate suppliers or executives to redirect international payments to offshore accounts.
- Cross-border financial crime involving crypto: use of international crypto exchanges, mixing services, and peer-to-peer platforms to move value across borders, often to convert illicit fiat proceeds or to cash out internationally.

The impact of cross-border fraud on businesses
Cross-border fraud inflicts direct and indirect harms. Direct financial losses include chargebacks, unpaid refunds, forced reimbursement of unauthorized transactions, and remediation costs. Indirect losses include customer churn, higher acquisition costs, increased compliance burden, and damage to corporate reputation that can impede growth in international markets.
For regulated financial services firms, consequences extend to enforcement actions, fines, and requirements for remediation imposed by supervisors. The operational cost of enhanced monitoring, transaction investigations, and cross-border legal work is also material – especially where cases require multilingual investigations and coordination with multiple authorities.
Smaller merchants and fintechs can suffer existential harm if attacks lead to suspended payment access or delisting from major platforms, making cross-border fraud a growth inhibitor for digital businesses seeking to scale internationally.
Red flags: How to spot cross-border fraud
While detection is never foolproof, several red flags reliably indicate heightened cross-border fraud risk.
- Unusual device or IP patterns: multiple payment attempts from devices geolocated in countries that don’t match the customer’s claimed residence.
- Inconsistent identity signals: discrepancies across identity documents, phone verification, email domains, and behavioral biometric patterns.
- Rapid account pattern changes: sudden increases in transaction volume, multiple rapid chargebacks, or new high-value payouts to unknown beneficiaries.
- Use of intermediate payment services or opaque payees: accounts routing funds through lesser-known PSPs or jurisdictions with weak transparency standards.
- Network indicators: known mule account patterns, reused shipping addresses, or clusters of accounts that show coordinated activity across borders.

Best practices for prevention and detection
Organizations can reduce exposure to cross-border scams by layering people, processes, and technology. Recommended practices include:
- Implement adaptive, risk-based KYC: use dynamic verification that increases scrutiny for higher-risk geographies, channels, or transaction types rather than a one-size-fits-all approach.
- Adopt identity orchestration and multi-factor signals: combine document verification, biometric checks, device intelligence, and transaction context to create stronger identity assurances across borders.
- Use transaction monitoring tuned for cross-border patterns: build rules and machine-learning models that detect routing anomalies, mule behavior, and cross-jurisdictional layering typical of international fraud.
- Strengthen partnerships and intelligence sharing: enter information-sharing agreements with other financial institutions, industry consortia, and law enforcement to speed detection and response to international threats.
- Deploy real-time sanctions, PEP, and adverse media screening that spans the jurisdictions where counterparties and payment routes operate.
- Harden merchant and payout workflows: require enhanced validation for high-risk payouts, use hold windows when suspicious patterns emerge, and apply graduated authentication for account changes tied to payments.
- Invest in cross-border fraud playbooks and exercises: practice coordinated incident response that includes legal, compliance, payments, and investigations teams to reduce the time to contain and remediate international incidents.
A practical checklist for businesses
Operational leaders can use this checklist to assess readiness and prioritize investments:
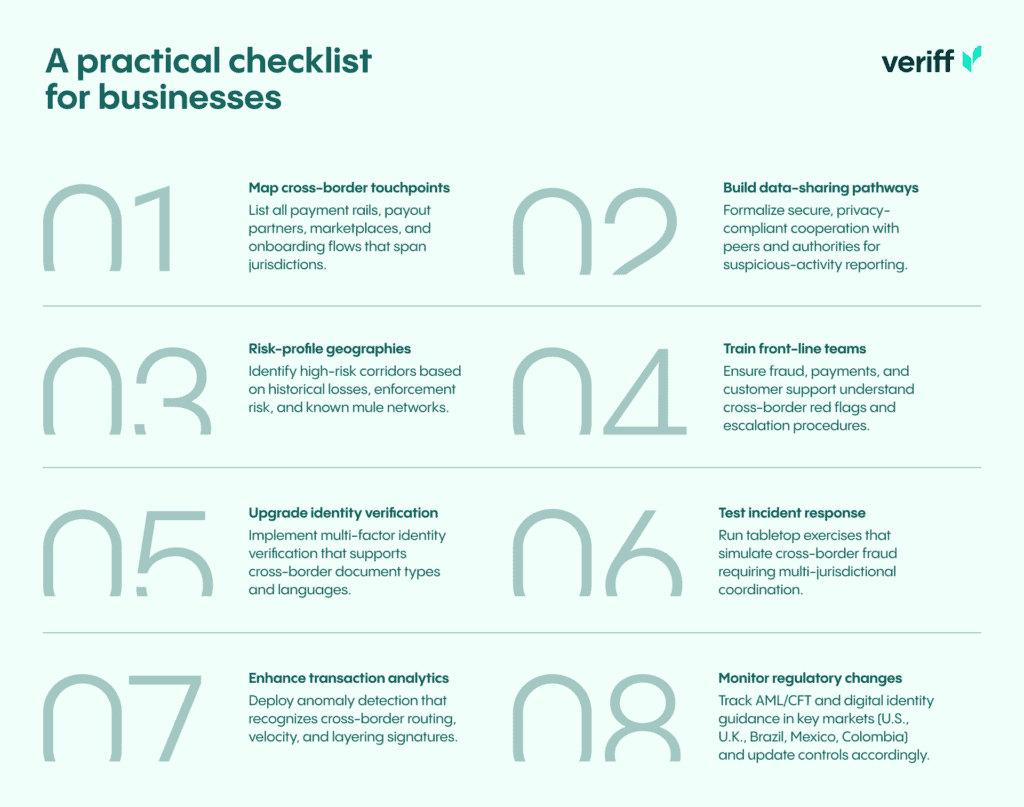
1) Map cross-border touchpoints: list all payment rails, payout partners, marketplaces, and onboarding flows that span jurisdictions.
2) Risk-profile geographies: identify high-risk corridors based on historical losses, enforcement risk, and known mule networks.
3) Upgrade identity verification: implement multi-factor identity verification that supports cross-border document types and languages.
4) Enhance transaction analytics: deploy anomaly detection that recognizes cross-border routing, velocity, and layering signatures.
5) Build data-sharing pathways: formalize secure, privacy-compliant cooperation with peers and authorities for suspicious-activity reporting.
6) Train front-line teams: ensure fraud, payments, and customer support understand cross-border red flags and escalation procedures.
7) Test incident response: run tabletop exercises that simulate cross-border fraud requiring multi-jurisdictional coordination.
8) Monitor regulatory changes: track AML/CFT and digital identity guidance in key markets (U.S., U.K., Brazil, Mexico, Colombia) and update controls accordingly.
Turning risk into opportunity
Managing cross-border fraud well isn’t just about loss prevention; it’s a competitive differentiator. Firms that build scalable, privacy-aware onboarding and robust cross-border controls can unlock faster market entry, reduced chargeback rates, and better customer trust. Effective fraud controls also streamline compliance and reduce the friction that often deters legitimate international customers.
Leading organizations use their fraud playbooks to inform product design – baking in adaptive KYC, layered authentication, and consolidated risk signals so global expansion is both faster and safer. They also leverage public-private partnerships, sharing indicators of compromise that raise collective defenses across corridors and ecosystems.
Building a safer global business
Cross-border fraud represents an evolving, systemic challenge for any business involved in international transactions. Its scale and complexity demand a strategic response that blends advanced identity verification, transaction monitoring, regulatory alignment, and active intelligence sharing. The best-defended firms view cross-border risk management as an enabler of growth rather than a drag on operations.
International fraud is rarely a single event – it’s a supply chain of stolen data, mule accounts, and weak controls. Addressing these supply chains requires closing gaps in KYC, accelerating cross-border cooperation, and deploying adaptable technology that scales across markets.
How Veriff can help?
Veriff provides advanced fraud prevention tools to help businesses detect and block fraudulent activities at scale. With 1,000+ risk signals analyzing device, network, and behavioral patterns, Veriff identifies high-risk activity and emerging fraud trends. Features like biometric authentication, global document coverage, and CrossLinks technology work together to prevent account takeovers, synthetic identities, and coordinated fraud attempts. Combined with AML and PEP screening, Veriff ensures compliance while safeguarding against financial crime and fraud, enabling secure and confident customer onboarding.
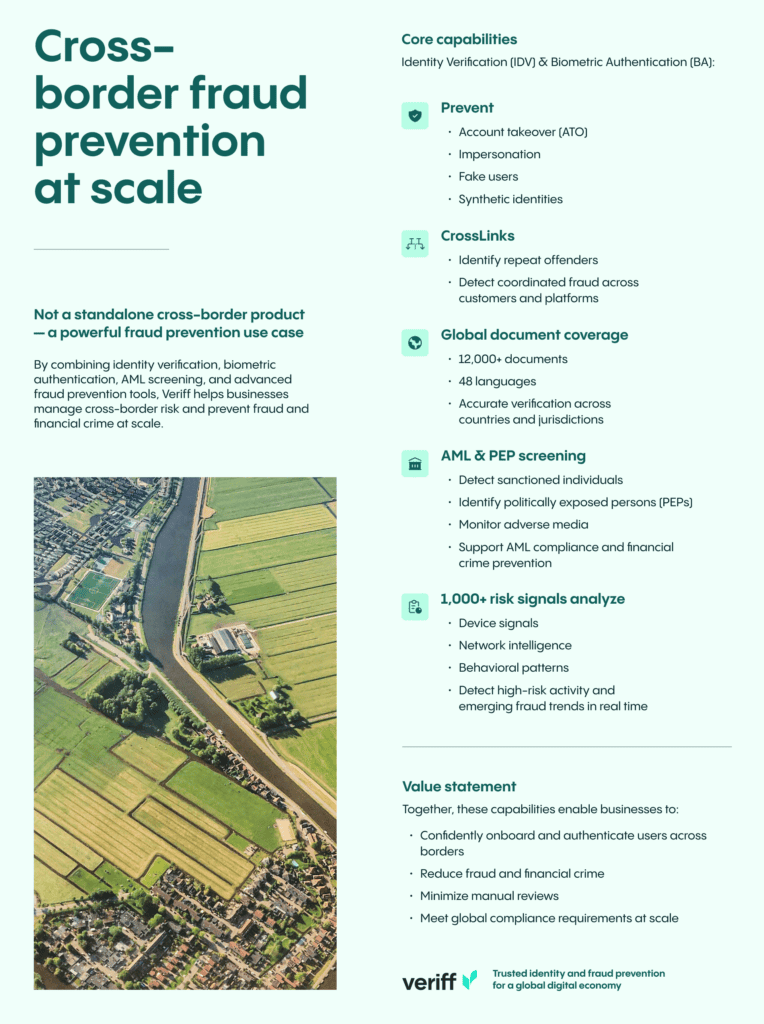
- Identity Verification (IDV) & Biometric Authentication (BA): Prevent account takeover (ATO), impersonation, fake users, and synthetic identities.
- CrossLinks: Identify repeat offenders and coordinated fraud across customers and platforms.
- Global document coverage (12,000+ documents; 48 languages): Verify genuine users across countries and jurisdictions with high accuracy.
- AML & PEP screening: Detect sanctioned individuals, politically exposed persons, and adverse media to help prevent money laundering.
- 1,000+ risk signals: Analyze device, network, and behavioral signals to detect high-risk activity and emerging fraud patterns across.
Together, these capabilities enable customers to confidently onboard and authenticate users across borders, while reducing fraud, minimizing manual reviews, and meeting compliance requirements.
Call to action: Protect your business with Veriff
Veriff helps financial services teams reduce the friction of compliant onboarding while minimizing exposure to cross-border fraud. By combining global document coverage, biometric verification, and contextual signals tailored for international transactions, Veriff enables firms to enforce risk-based controls across multiple jurisdictions and payment flows.

