Fraud Article
Key Insights from The Veriff Mobility Fraud Report January-June 2020
In our third fraud report, we take a look at the impact of online and identity fraud on the world of mobility in 2020, and the most prevalent types of fraud seen by Veriff, with data gathered from our verification flows.
Personal vehicle usage and public transport have transformed unimaginably in recent years, as innovative services like app-based cars, scooter or bike rentals, and ride-sharing have been introduced.
Such services led to the emergence of the concept of ‘Mobility-as-a-service’ (MaaS). In the “Technology in Society” journal the concept of MaaS is described simply as:
“The bundling of different transport means, public and private, into one easy-to-use package for the customer. The service is provided to the customer on demand via mobile applications and payment is handled via a digital wallet.”
In other words, MaaS brings all modes of transport together into one intuitive mobile app and makes any trip-planning easy and instant, putting the passenger at the forefront. It combines travel options with different vehicles from different carriers, providing everything from travel-planning to payment.
In addition to making travelling cheaper, easier and more accessible, the ‘MaaS’ concept also made it environmentally friendlier. The UK technology and innovation center for Intelligent Mobility has provided a theoretical example showing how a MaaS supporting user can reduce Single Occupancy Vehicle use in their report “Exploring the Opportunity for Mobility as a Service in the UK“.
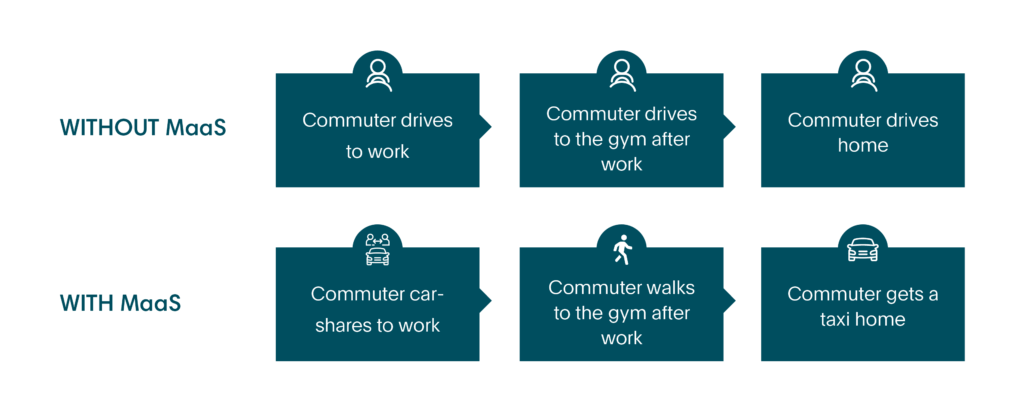
And according to the research of ‘Mobility and the Sharing Economy: Potential to Overcome First- and Last-Mile Public Transit Connections’, one-way car sharing is able to reduce VMT and GHG emissions by 6%-16% and 4%-18% accordingly.
The concept of shared consumption has changed the landscape of the mobility industry. It is based on the idea that sometimes temporary access to a service is more convenient and beneficial than permanent access. The shared consumption model has been proposed with regard to personal vehicle use for several years. The bottom line is this: there are hundreds of different vehicles scattered around a city (usually economical or electric cars, scooters or bikes) which can be easily booked and accessed directly from an app on your phone. And when the ride is finished, you lock the vehicle using the app, get a receipt and no longer worry about where you parked your car, how much the monthly maintenance is for it, etc.
When providing access to these services, you need to know your customer’s identity (and whether they’re allowed to use the relevant vehicle) before handing them the keys. This is where Veriff comes into play – helping you grant access to legitimate users with a high level of automation, accuracy, compliance and fraud prevention. And if you’re not convinced, check out what our partners, goUrban, said about us in our blog.
Impact of COVID-19 on Mobility
Mobility was one of the most affected industries during the COVID-19 pandemic. There are various factors at the heart of the negative consequences: lockdowns, closure of state borders, restrictions on movement, perceived health risk when using shared transportation etc. Different combinations of all of these factors affected every mobility service.
According to recent McKinsey analysis “With the number of passenger-kilometers traveled declining 50-60% worldwide since the onset of the COVID-19 crisis, use of micromobility solutions has declined dramatically.”
Today mobility companies are in a transitional stage full of uncertainty, with the potential need to introduce strict hygiene controls, such as compulsory face masks for drivers and passengers, health checks, protocols complying with distance and number of people allowed per space. The uncertainty concerns not only the timing of the return to pre-crisis indicators, but also the future image of the transport sector in the post-coronavirus world as a whole.
Veriff’s Fraud Prevention Tools
Veriff has an in-house built fraud prevention engine that is automating the decision making process and also assists specialists in case an automatic decision can’t be made (a hybrid approach). The engine can be broken into smaller pieces but all of them revolve around our proprietary device fingerprinting solution (see Graph 1).
Crosslinking
Crosslinking allows Veriff to group together sessions that share similar data points. Based on previous knowledge, fraudsters don’t tend to limit themselves to one try – they’ll try to get verified today, tomorrow and in the upcoming months and they won’t stop as long as they have fake identities. All the information from crosslinks is taken into account by our automatic decision engine, and is forwarded to our clients.
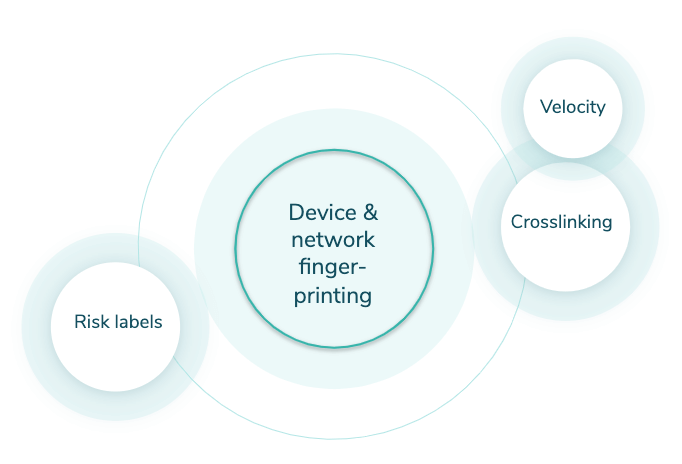
Graph 1. Veriff Fraud Prevention Engine
Velocity/Abuse
Velocity/Abuse ensures that no end-user abuses your service via multi-accounting. Taking into account all of the information we see through crosslinks, we can automatically shut down users if they, their document, or device have been approved before. We have three velocity checks that can be activated altogether or independently from each other:
- Duplicated user – checks whether the person has been approved before
- Duplicated document – checks whether the document has been approved before
- Duplicated device – checks whether the same device has been approved before
Risk labels
Risk labels point out the signs of fraudulent behavior in sessions. These labels are used by our specialists in more detailed security review and are forwarded to clients to give insight about the final decision and help in post analysis.
What types of fraud are we discussing here?
We’re breaking mobility fraud down into 4 main types:
- Document fraud
- Technical fraud
- Identity fraud
- Recurring fraud
We’ll look at each in depth, what they are, the types we see most regularly, and the impact within the financial technology world.
Document Fraud
This is often the type of identity fraud that leaps to mind first – tampered or entirely fake identity documents. These often exist in the form of fake IDs for a specific real world application – normally gaining access to something you’re underage for – but online there is normally more skill that goes into their creation, and they look to serve a monetary purpose, frequently some form of financial bonus on offer for inviting more users to a site.
In the case of mobility, we might consider a fake driver’s licence created to gain access to a vehicle when underage, or present when caught driving underage. Although both Veriff and police forces can catch these out with impressive speed.
Tampered documents
There are various methods of tampering, but the end result always includes slight alterations made to a legitimate document in order to partially or entirely change the holder’s identity. Forgeries include but are not limited to:
- Altering or replacing the document image
- Overwriting document data with a pen, pencil or other simple tools
- Adding/removing specific document data or elements
Fake documents
Tampered documents are usually counterfeit originals, but fake documents try to imitate the appearance of a legitimate-looking document but are reproductions of the original. These come in the form of:
- Alterated government-issued specimens that are public
- Premade templates with fake photos and data
In the first 6 months of 2020, document fraud represented 7% of all fraud in the mobility market (see Graph 2).
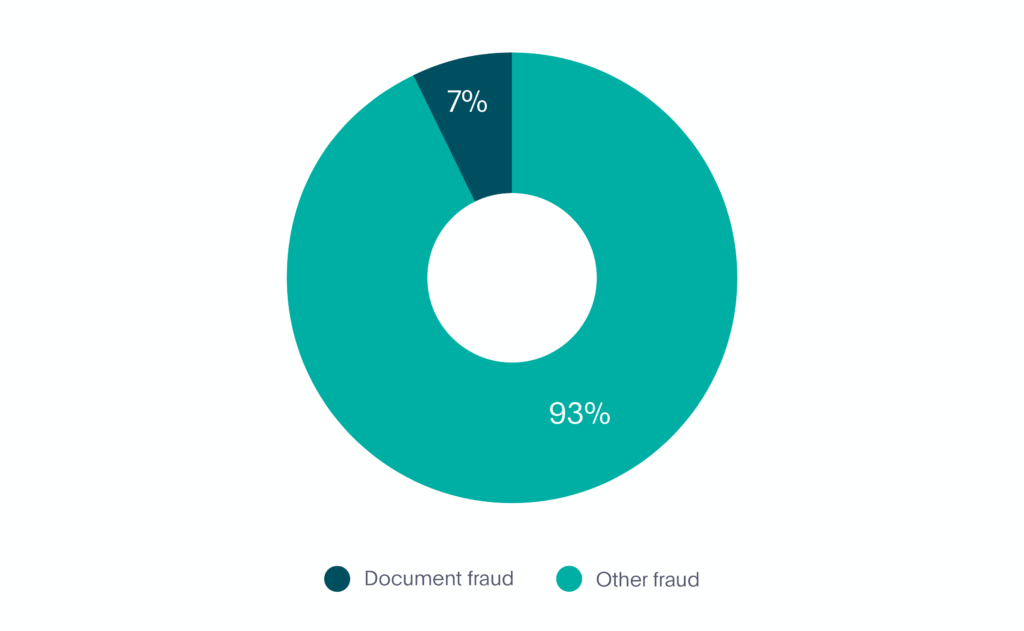
Graph 2. Document Fraud in Mobility
How Veriff tackles document fraud
Our in-house document database plays a key role in ensuring the accuracy of document fraud prevention. The database is updated regularly as we carry out extensive document related research (i.e. we find official specimens, information related to the issuing terms, etc) and cooperate with government authorities across the world.
In addition to our database, Veriff’s in-house fraud prevention engine plays a crucial role in document fraud detection and prevention. With the help of crosslinking we’re able to see if a user has previously submitted tampered documents or was involved in any suspicious activity.
Technical Fraud
This is exactly what you’d perhaps expect, fraud which involves a degree of technical skill which an average person wouldn’t possess. In this instance, we’re looking at streamed images and fraudulent access, two methods to take advantage of offers and make potential monetary gains.
Images and/or videos are streamed (or a slideshow)
This type of fraud happens when a verification includes media that’s coming from an emulated camera source. A fraudster might collect the portrait and document pictures belonging to different people in advance, edit them into a video and stream this inside Veriff’s flow to imitate the process being live.
Fraudulent access to the session
Every time an end-user accesses the verification flow, we collect device and network information. Fraudulent accesses are defined as:
“Accesses associated with one verification session that has been accessed from different countries’ networks and multiple devices.”
This is an indicator of the session link being fraudulently shared between different parties.
In the first 6 months of 2020, technical fraud represented 4% of all fraud in the mobility market (see Graph 3).
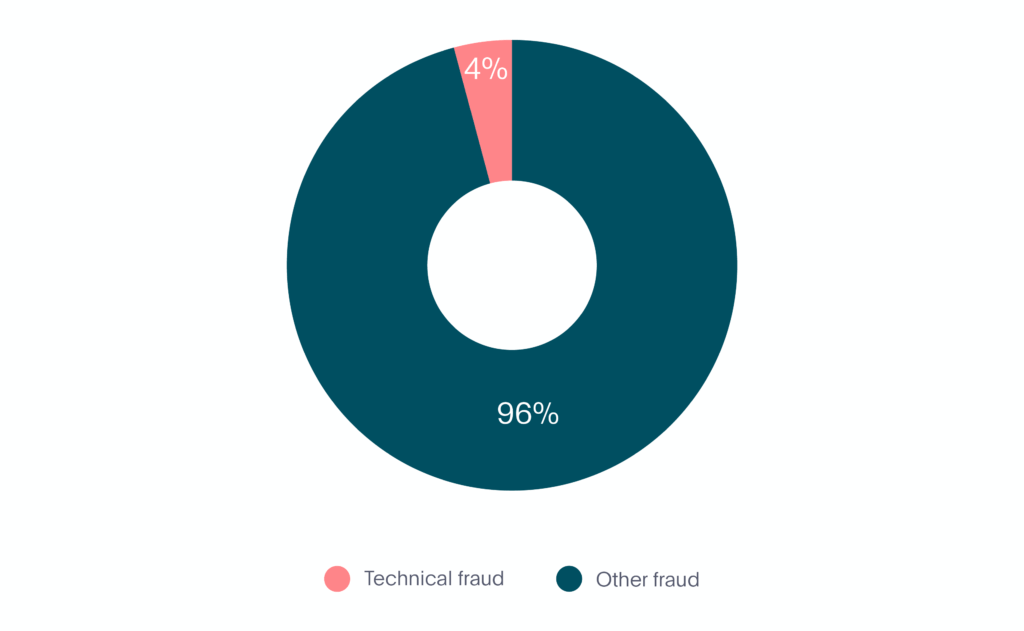
Graph 3. Technical Fraud in Mobility
How Veriff tackles technical fraud
Our comprehensive profile of raw device and network data grants us full control over exactly which pieces of information we use and in what context. We can utilize specific elements of the device information, to spot whether camera emulation software was used at some point during the verification process.
If we detect that an emulated camera source was used to submit the session, we note this, which helps in the final decision. We also perform checks on session images, to check if there is consistent natural movement between them.
To prevent possible fraudulent access in the session, we look to detect whether a session is being accessed from different countries’ networks. If we detect a repetitive pattern indicating fraudulent access, we automatically block the user with the suspicion of the session link being compromised.
As we’re talking about technical fraud – did you know about the existence of romance scams?
In romance scams fraudsters usually create fake online profiles with fictional identities, pictures and names with the help of which they lure their victims, where the main target group is usually senior women. After contact is established, they start expressing strong emotions for their victim, sharing ‘personal’ information and digitally whispering sweet nothings. Once they’ve gained their victims’ trust, they request for money or other ‘favors’. These scams usually end up with big financial losses and a deep emotional feeling of betrayal.
We’ve unsurprisingly seen a similar ‘love story’ in Veriff. A woman was lured into opening an account for a service we assumed she would never use, most likely not understanding she’s the victim of a scam. Thanks to our fraudulent access detection and video feature, we caught the fraudster red-handed while he was asking the woman to take additional pictures and send authorization details via messenger.
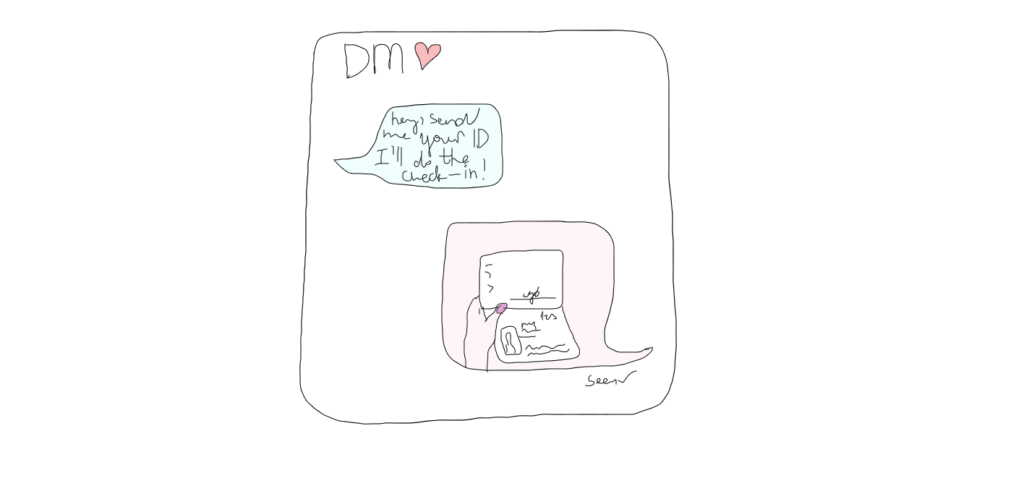
Image by Miina Vilo
Identity Fraud
Now we come to identity fraud. Not dissimilar to document fraud which we mentioned earlier, identity fraud is more about impersonation than actual document tampering. That’s one of the two examples we’ll look to highlight in fact, attempted impersonation, along with attempted deceit.
Attempted impersonation
Attempted impersonation is the intentional use of someone else’s identity document with the aim of obtaining access to the service on someone else’s behalf. This type of fraud usually uses an illegally obtained physical document of the victim presented by a fraudster.
Attempted deceit using fake images
The end-user doesn’t show a real physical document, but shows it from a device screen or a printed-out paper as they’re using someone else’s digital document or a digitally manipulated document of their own.
In the first 6 months of 2020, identity fraud made up 55% of all fraud in the mobility market making it by far the most prevalent type (see Graph 4).
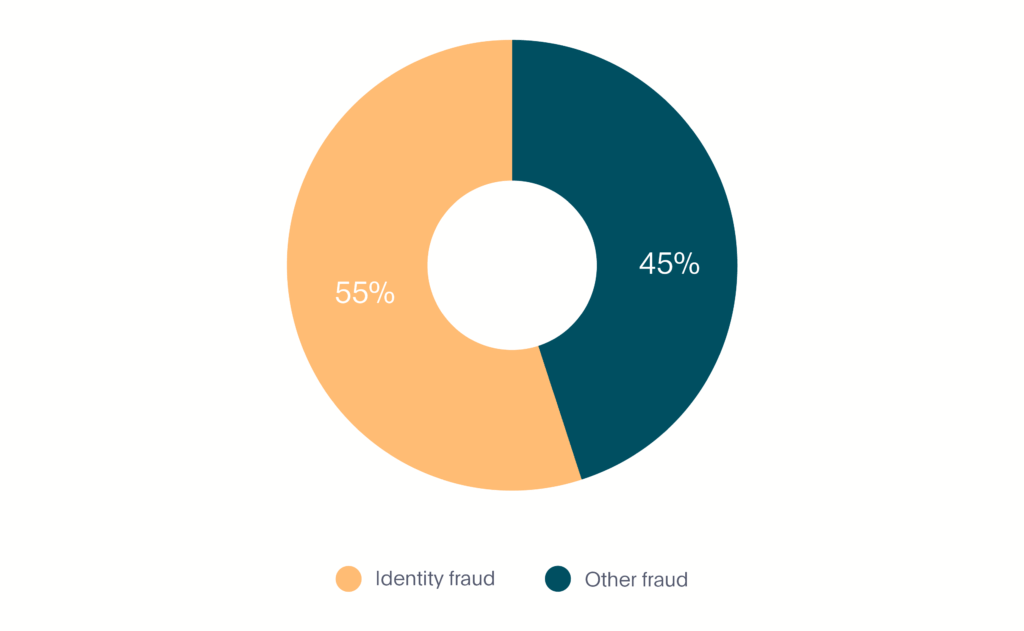
Graph 4. Identity Fraud in Mobility
How Veriff fights identity fraud
Given the nature of the industry, every mobility company has to keep a balance between ensuring compliance with all the relevant regulations and offering a great customer experience. And this is where Veriff comes in, with our highly configurable flow and strong fraud prevention.
In order to detect whether a verification process has been initiated with someone else’s physical document, we compare extracted faces from a selfie and a document photo. If our confidence in the similarity is too low we decline the session. If our automated engine is unsure it highlights appropriate risks and leaves the decision to a specialist.
For mobility, we’re predominantly verifying driver’s licenses, and this is why we also now offer driver’s license category extraction, as an additional feature geared towards mobility companies. You’ll not only be able to see the details of your user, but also what category of vehicle they’ve been approved to drive.
By providing high-value assets to consumers, namely cars, every mobility service is subject to high business risks. Along with a potential vehicle’s theft there is the danger of identity theft by fraudsters who penetrate real users’ devices or create fake identities to get access to the service.
“Identity theft is not a joke, Jim! Millions of families suffer every year!“ – Dwight Schrute
Here in Veriff, we’ve seen different types of identity theft – from underage kids using their siblings’ or parents’ documents to rent a scooter to deepfakes trying to imitate someone else’s likeness by manipulating images and/or videos. The rising tide of AI and machine learning is constantly making it easier to steal someone’s face without undergoing a plastic surgery (like John Travolta did in the movie “Face/Off”), but our anti-spoofing controls and deepfake detection will make sure the right person is getting access to the service they require.

An example of deepfake technology: in a scene from Man of Steel, actress Amy Adams in the original (left) is modified to have the face of actor Nicolas Cage (right) – source https://en.wikipedia.org/wiki/Deepfake
Recurring Fraud
Finally, we come to recurring fraud. This is also broken down into two examples, one of which is basic ‘recurring’ fraud, where a fraudster has been successful and come back to try again. The other is velocity abuse, which we’ll explain further below.
Recurring – Strong links to previous fraud
If fraudsters manage to abuse the system – they will come back and try again, if they fail to do so – they will come back and try twice as hard.
Velocity abuse
Velocity abuse works as follows – after getting approved once, fraudsters try to abuse the system and get approved as many times as possible, which usually involves verifying different real users without telling them what they’re being verified for. Fraudsters tend to go as far as creating synthetic identities, where they try to create a new identity by combining their real information in conjunction with fake data.
In the first 6 months of 2020, recurring fraud made up 34% of all fraud in the mobility market (see Graph 5).
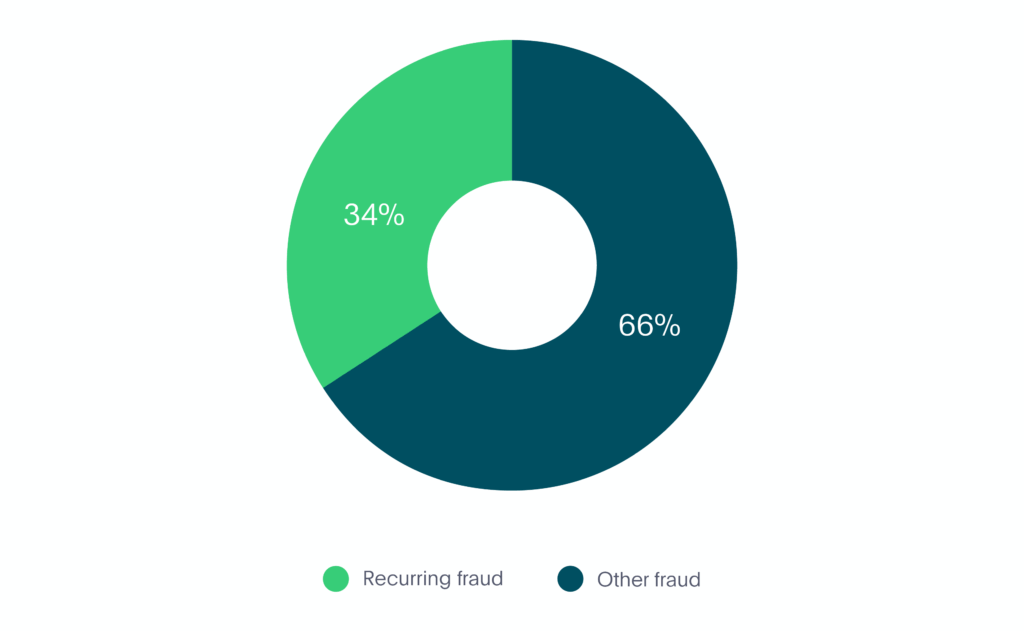
Graph 5. Recurring Fraud in Mobility
How Veriff fights recurring fraud
Recurring fraud is where our crosslinks shine the brightest. If we’re confident that the end-user has committed fraud before, we’ll automatically decline all the recurring attempts associated with the same person, device or document.
If the same person, document or device have been found approved in the historically submitted sessions, all the recurring attempts will be declined with Velocity/Abuse.
The Overall Breakdown
Now that we’ve looked at the 4 different types of fraud that we’ve seen within the mobility industry, we can see the full breakdown below (see Graph 6):
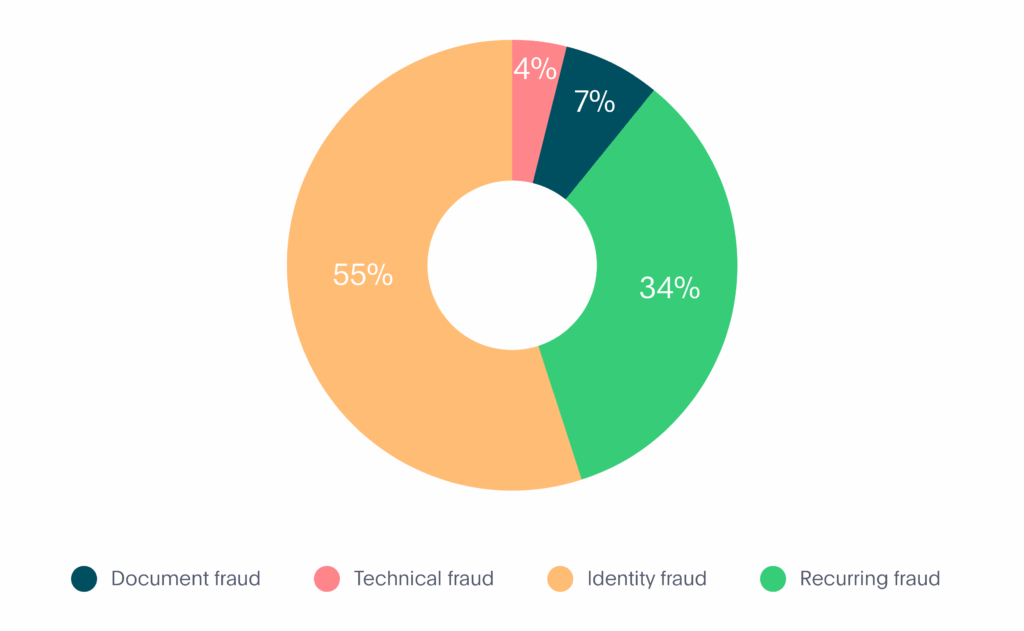
Graph 6. Fraud Types in Mobility
- Document fraud – 7%
- Technical fraud – 4%
- Identity fraud – 55%
- Recurring fraud – 34%
Of course in all of the above instances, Veriff is well-placed as a verification provider to fight back against online fraud in all forms. We continue to observe trends across the mobility industry so we can stay ahead of developments, and prevent problems for our mobility partners.
Talk to us
If you’d like to learn more about Veriff’s fraud prevention technology, you can visit our website or contact us via (email here). And make sure to look out for our final report coming in the near future – covering all the 3 industries (Crypto, Fintech & Mobility) in one overall exhaustive report.

