IDV Article
How to verify user identity: A guide to secure and seamless onboarding
A blog about user identity, including popular verification methods, why verifying user identity is important, and the role of verifying user identity in relation to global compliance.
As a fraud and risk leader, ensuring your business stays ahead of fraudsters while maintaining a frictionless customer experience is a daily challenge. With 21% year-over-year growth in online fraud (Veriff’s 2024 Fraud Report) and the rise of deepfakes, synthetic identities, and social engineering, you need solutions that not only meet regulatory demands but also build a strong case for internal buy-in.
For leaders like you—Heads of Fraud, AML Compliance, Risk, and Trust & Safety—identity verification (IDV) is more than just a compliance checkbox. It’s about balancing security, user experience, and business impact, all while ensuring executive stakeholders see its value. This guide breaks down the latest fraud trends, effective IDV strategies, and key insights to help you drive internal support for fraud prevention initiatives.
What is user Identity Verification, and why should you advocate for it?
The Federal Trade Commission’s (FTC) recent report reveals that consumers reported losing $12.5 billion to fraud in 2024, a 25% increase from the previous year.
With regulations tightening worldwide and cyber threats becoming more sophisticated, organizations must deploy effective IDV solutions to protect their businesses, customers, and reputations. If you run an online business, ensuring your customers are who they claim to be is not just a security measure—it’s a business imperative. From preventing fraud to ensuring regulatory compliance, identity verification (IDV) is critical for businesses operating in financial services, online gaming, mobility, and other regulated industries.
Identity verification (IDV) is the process of ensuring an individual is who they claim to be. For fraud and risk teams, this means mitigating financial and reputational risks, ensuring compliance with AML (Anti-Money Laundering), KYC (Know Your Customer) regulations, and building internal confidence in fraud prevention measures.
Common business challenges IDV solves:
✔ Risk to your personal reputation: Recommending ineffective fraud prevention solutions can undermine trust in your expertise.
✔ Building a strong business case: Proving IDV’s impact on fraud prevention, compliance, and conversion rates.
✔ Convincing internal stakeholders: Demonstrating ROI and operational efficiency to decision-makers.
✔ Managing stakeholder resistance: Overcoming concerns about implementation complexity or customer friction.
Identity Verification methods: Finding the right fit
Every business has unique fraud risks, but not all IDV methods provide the same level of security and user experience. Here’s how to choose the right fit for your organization:
1. Biometric Authentication
Biometric authentication verifies an individual’s identity based on unique biological characteristics. It is a highly secure and user-friendly method that reduces friction while ensuring high accuracy. Biometric IDV solutions can lower fraud rates while streamlining onboarding—helping fraud prevention teams make a case for adoption.
✔ Facial recognition with liveness detection ensures fraudsters can’t use fake photos or videos.
✔ Automated decision-making improves speed and reduces manual review costs.
✔ Industry leaders are already adopting this: Financial institutions, fintechs, and online platforms see reduced fraud rates.
With deepfake attacks increasing by 300% in 2024, businesses must ensure their biometric authentication systems incorporate liveness detection to prevent spoofing attempts. Watch our video with Chris Hooper and Geo Jolly to explore biometrics, AI, and the future of fraud prevention:
The intersection of AI and biometrics is reshaping the future of identity verification, bringing both enhanced security and new challenges. AI-driven biometric authentication is becoming a key pillar in identity verification strategies, offering seamless and highly accurate user authentication. However, the rise of deepfake technology and sophisticated spoofing attacks has made it critical for businesses to integrate advanced liveness detection and AI-powered fraud prevention measures. As AI algorithms improve, biometric systems are evolving to detect anomalies, prevent identity fraud, and ensure regulatory compliance. Businesses that leverage AI-enhanced biometrics can significantly reduce onboarding friction while maintaining high security, making this technology a crucial component of modern identity verification solutions.
2. Online ID Verification
Online verification systems validate government-issued IDs by comparing them with real-time selfies or video captures. Veriff’s AI-powered verification platform ensures:
✔ Validates government-issued IDs against databases in real-time.
✔ Improves compliance with AML, KYC, and age verification laws.
✔ Minimizes friction with instant verification decisions.
3. Two-Factor Authentication (2FA)
2FA enhances security by requiring an additional verification step, such as a one-time password (OTP) sent via SMS or email. Many financial institutions now incorporate biometric 2FA for added protection.
✔ Adds an extra layer of security beyond passwords.
✔ Many businesses now combine biometric authentication with 2FA for enhanced fraud prevention.
2FA alone isn’t enough, but combining it with AI-powered IDV provides a robust fraud prevention strategy.

Uncover the Latest Identity Fraud Trends
Get exclusive insights into the evolving fraud landscape and how businesses can stay ahead in 2025.
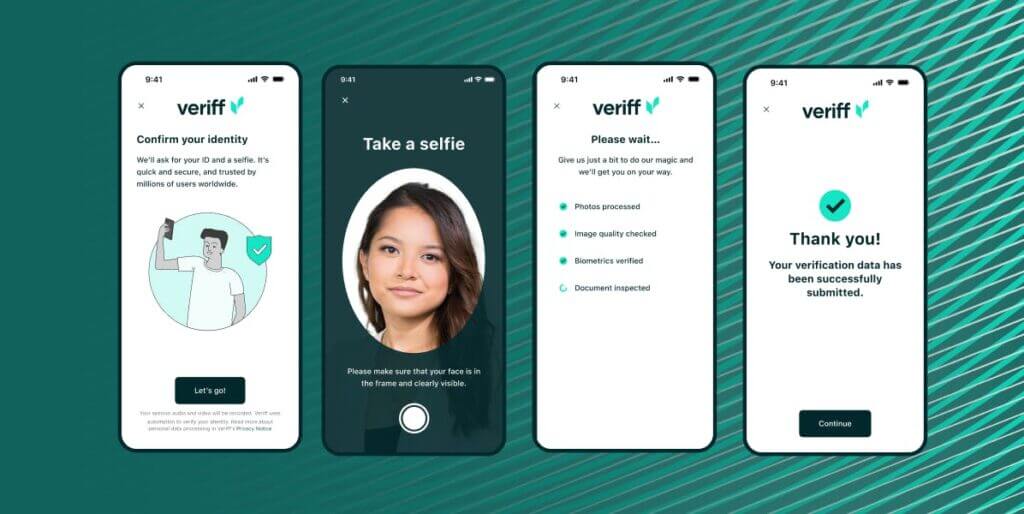
How the IDV process works: A step-by-step guide
✔ User submits a photo of their ID. Veriff’s system automatically identifies the document type and checks for authenticity.
✔ User takes a live selfie. Advanced AI ensures that the selfie matches the ID photo.
✔ Verification decision is made. The system evaluates the document and biometric data.
✔ Customer is onboarded. The verified user gains access to services securely.
With AI-powered identity verification, businesses can reduce fraud risks while streamlining the onboarding process—helping to build a safer, more trustworthy online ecosystem.
How financial services in the UK are strengthening security with Identity Verification
One of the most critical industries requiring robust identity verification is financial services, where security and compliance are paramount. In our UK financial services case study, we explore how leading institutions like Crown Agents Bank, Griffin, Finst, Fundvest, and Monese have successfully implemented digital identity verification to enhance security, streamline customer onboarding, and combat fraud. By leveraging AI-powered verification, these companies have improved trust and compliance while ensuring a seamless user experience. Their success highlights the growing need for businesses to adopt advanced identity verification solutions to protect customers and meet regulatory requirements.
Listen to the full Veriff Voice´s conversation with Chris and Bonnie now.

What we really like about Veriff’s technology is that it keeps the end user within the journey. It doesn’t allow the individual to get right to the end of the process and say, “Sorry, this hasn’t worked”. Instead, it guides them using assisted image capture along the way. It holds their hand – and that’s exactly what, with our demographic, we need it to do.
IDV that works for your business
Every organization has a unique view of how to balance speed, conversion, and fraud mitigation during the identity verification process. That´s why Veriff offers the following options:
Veriff offers two identity verification (IDV) solutions tailored to different business needs: Full Auto and Hybrid. The Full Auto solution is a fully automated AI-driven verification system designed for businesses prioritizing speed, high conversion rates, and cost efficiency. It offers a 6-second verification speed, good accuracy, and enhanced risk insights with RiskScore availability, making it ideal for companies that need rapid and seamless verification processes. On the other hand, the Hybrid solution combines advanced AI technology with expert verification specialists, ensuring higher accuracy, enhanced fraud prevention, and additional security through human oversight. This option is best suited for organizations that require a balance between speed and security, providing fraud prevention reassurances and risk insights. Both solutions enable businesses to streamline their IDV process while mitigating fraud risks, ultimately enhancing customer trust and regulatory compliance.
Final thoughts: The future of Identity Verification
As fraud tactics become more sophisticated, businesses face mounting pressure to stay ahead with cutting-edge identity verification (IDV) technologies. The rise of threats like deepfakes and synthetic identity fraud underscores the urgency for real-time biometric authentication and continuous monitoring to catch anomalies before they escalate into serious issues.
However, embracing advanced IDV solutions has its own challenges. Businesses risk damaging their personal reputation if the wrong decision is made when selecting a solution. Building a strong business case for internal buy-in and convincing key stakeholders, especially the Economic Buyer, can be daunting. Additionally, managing stakeholder resistance to new technology often becomes a roadblock that slows down progress.
Businesses must prioritize advanced, AI-powered IDV platforms like Veriff to safeguard customers, ensure compliance, and build trust—all while overcoming internal challenges and delivering a frictionless user journey. With the stakes higher than ever, staying ahead in the fight against fraud has never been more critical.

