Fraud Article
Veriff Fintech Fraud Report: January to June 2020
In our second fraud report, we take a look at the impact of financial crime and fraud on the world of fintech in 2020, and the most prevalent types of fraud seen by Veriff, with data gathered from our verification flows.
The Financial Technology (Fintech) industry has been gaining momentum over the years by transforming the way financial businesses operate and providing a huge range of services to consumers. The industry has evolved rapidly and keeps on growing. According to the ‘Fintech Global Market Opportunities and Strategies‘ report published in July 2020:
“The global Fintech market reached a value of nearly $111,240.50 million in 2019, having grown at a compound annual growth rate (CAGR) of 7.9% since 2015, and is expected to grow at a CAGR of 9.2% to nearly $158,014.3 million by 2023. Also the market is expected to grow to $191,840.2 million in 2025 at a CAGR of 10.2% and to $325,311.8 million in 2030 at a CAGR of 11.1%.”
Fintech transforms traditional banks into faster, more secure and coherent businesses by implementing technologies like Blockchain and AI. Fintech refers to any app, software, or technology that allows people or businesses to digitally access, manage, or gain insights into their finances or make financial transactions. It enabled the possibility of day-to-day banking operations, trading, investing, lending, international payments etc to users all around the world. Moreover, according to the World Bank Group report, digital financial services have the potential to help the poor increase their income and resilience by gaining access to basic financial services and mobile banking.
However we’ve seen the potential for fraud and financial abuse within the industry, with the recent Wirecard story acting as a stark reminder to up-and-coming players in the financial world of having risk management protocols in place. But this was fraud on a large scale – what about the everyday fraudsters, intentionally attempting to steal identities in an attempt to gain access to accounts or gain financial windfalls? This can include personal information like addresses, phone numbers and credit card numbers. This is what Veriff is fighting daily.
Impact of COVID-19 on Fintech
The COVID-19 pandemic hit most industries incredibly hard. It impacted the financial stability of business as well as individuals, sending millions to poverty. According to the Global Economic Prospects the crisis is expected to leave a 5.2% contraction on global economic activity in 2020.
At the same time the crisis brought an opportunity for Fintech companies to increase their demand in times of social distancing, quarantines and people adapting to a new reality powered by digitization. The openness of blockchain technology means that money laundering has almost become a spectator sport in some corners of the internet. We’ve written on our blog about how the pandemic will impact the future of the financial industry and measures to combat illicit financing.
As many businesses look to go digital, the demand for digital KYC processes also increases. And this is where Veriff comes in by helping granting access to services to legitimate users, and blocking the fraudsters accessing investment management systems.
Veriff’s Fraud Prevention Tools
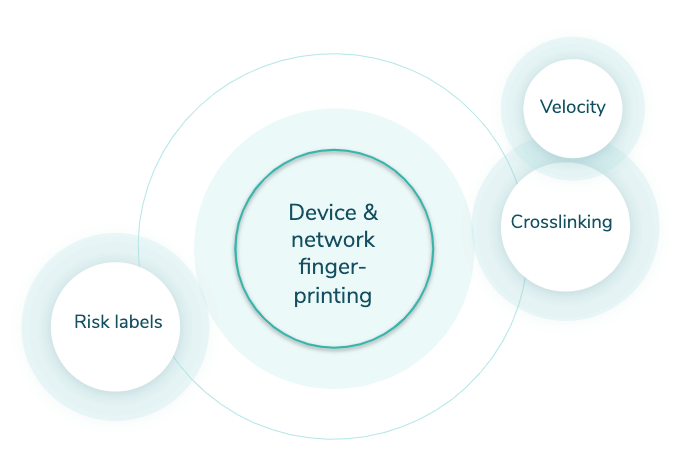
Veriff has an in-house built fraud prevention engine that is automating the decision making process and also assists specialists in case an automatic decision can’t be made (a hybrid approach). The engine can be broken into smaller pieces but all of them revolve around our proprietary device fingerprinting solution (see Graph 1).
Crosslinking
Crosslinking allows Veriff to group together sessions that share similar data points. Based on previous knowledge, fraudsters don’t tend to limit themselves to one try – they’ll try to get verified today, tomorrow and in the upcoming months and they won’t stop as long as they have fake identities. All the information from crosslinks is taken into account by our automatic decision engine, and is forwarded to our clients.
Graph 1. Veriff Fraud Prevention Engine
Velocity/Abuse
Velocity/Abuse ensures that no end-user abuses your service via multi-accounting. Taking into account all of the information we see through crosslinks, we can automatically shut down users if they, their document, or device have been approved before. We have three velocity checks that can be activated altogether or independently from each other:
- Duplicated user – checks whether the person has been approved before
- Duplicated document – checks whether the document has been approved before
- Duplicated device – checks whether the same device has been approved before
Risk labels
Risk labels point out the signs of fraudulent behavior in sessions. These labels are used by our specialists in more detailed security review and are forwarded to clients to give insight about the final decision and help in post analysis.
What types of fraud are we discussing here?
We’re breaking Fintech fraud down into 4 main types:
- Document fraud
- Technical fraud
- Identity fraud
- Recurring fraud
We’ll look at each in depth, what they are, the types we see most regularly, and the impact within the financial technology world.
Document Fraud
This is often the type of identity fraud that leaps to mind first – tampered or entirely fake identity documents. These often exist in the form of fake IDs for a specific real world application – normally gaining access to something you’re underage for – but online there is normally more skill that goes into their creation, and they look to serve a monetary purpose, frequently some form of financial bonus on offer for inviting more users to a site.
So let’s look at both examples.
Tampered documents
There are various methods of tampering, but the end result always includes slight alterations made to a legitimate document in order to partially or entirely change the holder’s identity. Forgeries include but are not limited to:
- Altering or replacing the document image
- Overwriting document data with a pen, pencil or other simple tools
- Adding/removing specific document data or elements
Fake documents
Tampered documents are usually counterfeit originals, but fake documents try to imitate the appearance of a legitimate-looking document but are reproductions of the original. These come in the form of:
- Alterated government-issued specimens that are public
- Premade templates with fake photos and data
In the first 6 months of 2020, document fraud represented 24% of all fraud in the fintech market (see Graph 2).
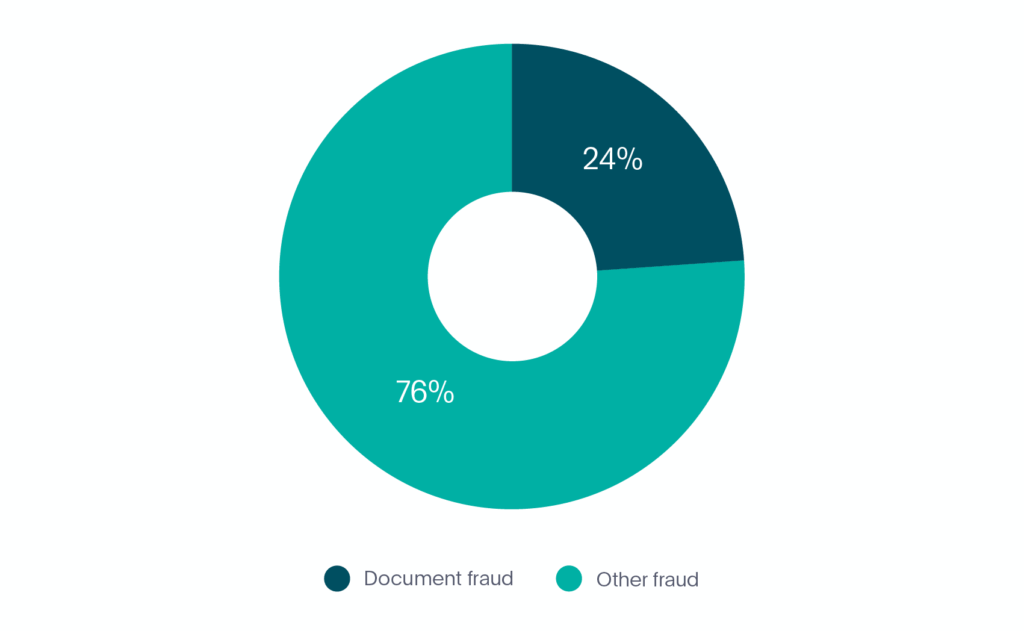
Graph 2. Document fraud in fintech
How Veriff tackles document fraud
Our in-house document database plays a key role in ensuring the accuracy of document fraud prevention. The database is updated regularly as we carry out extensive document related research (i.e. we find official specimens, information related to the issuing terms, etc) and cooperate with government authorities across the world.
In addition to our database, Veriff’s in-house fraud prevention engine plays a crucial role in document fraud detection and prevention. With the help of crosslinking we’re able to see if a user has previously submitted tampered documents or was involved in any suspicious activity.
Document fraud is the second most prevalent type of fraud in Fintech, so no matter which area you’re in, we’re ready to help you tackle this problem. And trust us, we’ve seen different types of document tampering, from very obvious one-time document manipulation to complex fraud schemes, like the following:
”We noticed unusual traffic coming from an Eastern European country, associated with a financial institution. What raised suspicions even further was the fact that customers were submitting documents issued by a different country. At first glance one could think these were people travelling, as the documents seemed legitimate and people presenting them matched the identity on the document. But having all data points collected by our fraud engine and our highly trained specialists’ expertise, it became evident that the presented documents were fake, and the end-users presenting them were up to something fishy. Our further investigation revealed that the group of fraudsters used disposable tools in order to emulate foreign traffic and create the illusion of “legitimacy”, and we had a reason to believe that the ultimate goal of this scheme was to set people up for migration to a more developed country (with fake documents in hand and a financial history). Unfortunately for these people, the trip was short lived.”

Image by Miina Vilo
Technical Fraud
This is exactly what you’d perhaps expect, fraud which involves a degree of technical skill which an average person wouldn’t possess. In this instance, we’re looking at streamed images and fraudulent access, two methods to take advantage of offers and make potential monetary gains.
Images and/or videos are streamed (or a slideshow)
This type of fraud happens when a verification includes media that’s coming from an emulated camera source. A fraudster might collect the portrait and document pictures belonging to different people in advance, edit them into a video and stream this inside Veriff’s flow to imitate the process being live.
Fraudulent access to the session
Every time an end-user accesses the verification flow, we collect device and network information. Fraudulent accesses are defined as:
“Accesses associated with one verification session that has been accessed from different countries’ networks and multiple devices.”
This is an indicator of the session link being fraudulently shared between different parties.
In the first 6 months of 2020, technical fraud represented 1% of all fraud in the fintech market (see Graph 3).
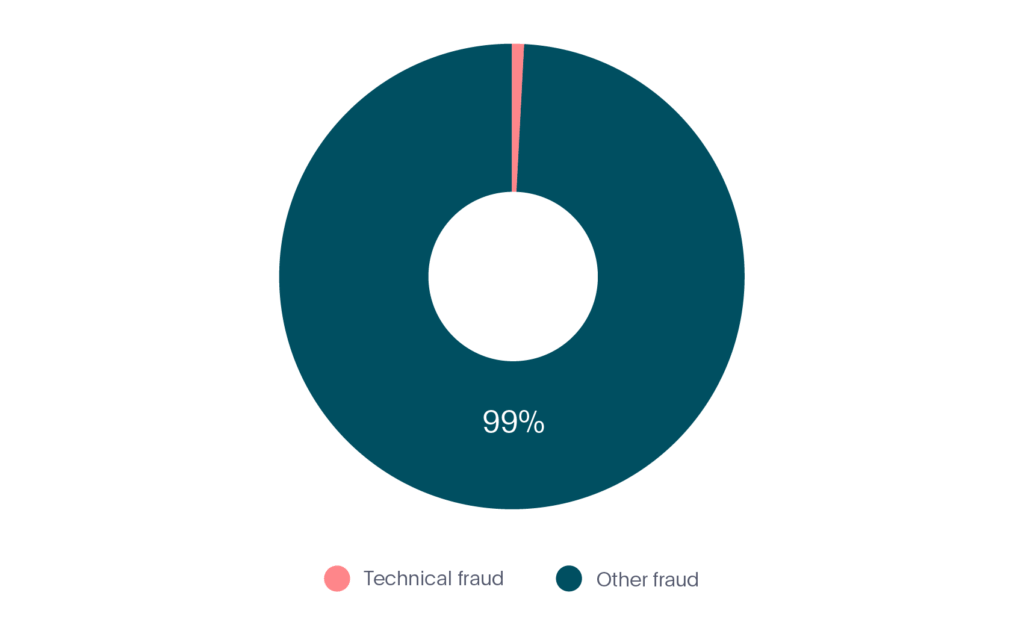
Graph 3. Technical fraud in fintech
How Veriff tackles technical fraud
Our comprehensive profile of raw device and network data grants us full control over exactly which pieces of information we use and in what context. We can utilize specific elements of the device information, to spot whether camera emulation software was used at some point during the verification process.
If we detect that an emulated camera source was used to submit the session, we note this, which helps in the final decision. We also perform checks on session images, to check if there is consistent natural movement between them.
To prevent possible fraudulent access in the session, we look to detect whether a session is being accessed from different countries’ networks. If we detect a repetitive pattern indicating fraudulent access, we automatically block the user with the suspicion of the session link being compromised.
Identity Fraud
Now we come to identity fraud. Not dissimilar to document fraud which we mentioned earlier, identity fraud is more about impersonation than actual document tampering. That’s among the examples we’ll look to highlight in fact, attempted impersonation. We’ll also look at third party guidance, which involves a more physical presence.
Attempted impersonation
Attempted impersonation is the intentional use of someone else’s identity document with the aim of obtaining access to the service on someone else’s behalf. This type of fraud usually uses an illegally obtained physical document of the victim presented by a fraudster.
Attempted deceit using fake images
The end-user doesn’t show a real physical document, but shows it from a device screen or a printed-out paper as they’re using someone else’s digital document or a digitally manipulated document of their own.
Third party guidance
Third party guidance usually involves physical assistance of the end-user, sometimes without telling them what the verification is for. This behavior leads us to believe that the end-user being assisted will not be the one actually using the service they’re being signed up for.
In the first 6 months of 2020, identity fraud made up 67% of all fraud in the fintech market making it by far the most prevalent type (see Graph 4).
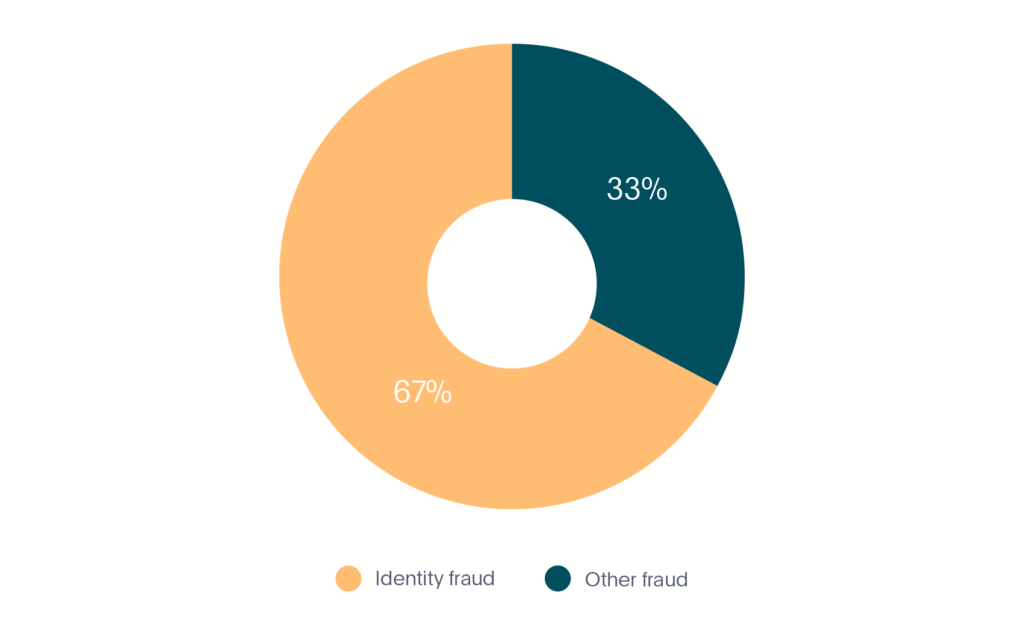
Graph 4. Identity fraud in fintech
How Veriff fights identity fraud
Given the nature of the industry, every Fintech startups have to keep a balance between ensuring compliance with all the relevant regulations and offering a great customer experience. And this is where Veriff comes in, with our highly configurable flow and strong fraud prevention.
In order to detect whether a verification process has been initiated with someone else’s physical document, we compare extracted faces from a selfie and a document photo. If our confidence in the similarity is too low we decline the session. If our automated engine is unsure it highlights appropriate risks and leaves the decision to a specialist.
It’s no wonder identity fraud is the most prominent type of fraud in fintech. Malicious actors’ appetite grows together with the industry, as more and more services are digitized and clients don’t have to physically meet a financial representative anymore to open accounts or perform any financial transactions. Here’s another first-hand story from inside Veriff:
“Forging a photo on a document is one thing, but forging the person presenting the document is a whole other story! The villain of this story must have watched the episode of “The Office” (the US version), where Dwight Schrute demonstrated his collection of wigs for every single person in the office with the words: “You never know when you’re gonna need to bear a passing resemblance to someone”. Our perpetrator printed out a document with a nicely crafted face on it, and in addition, has designed a life-like mask matching the identity on the document he was showing. If only he knew we were able to see him ‘changing faces’, he probably wouldn’t have gone this far.”
Don’t miss the chance to explore the latest trends and gain financial advice and actionable insights essential for combating fraud and protecting your business for financial inclusion. Download our Identity Fraud Report 2024 today.

Image by Miina Vilo
Recurring Fraud
Finally, we come to recurring fraud. This is also broken down into two examples, one of which is basic ‘recurring’ fraud, where a fraudster has been successful and come back to try again. The other is velocity abuse, which we’ll explain further below.
Recurring – Strong links to previous fraud
If fraudsters manage to abuse the system – they will come back and try again, if they fail to do so – they will come back and try twice as hard.
Velocity abuse
Velocity abuse works as follows – after getting approved once, fraudsters try to abuse the system and get approved as many times as possible, which usually involves verifying different real users without telling them what they’re being verified for. Fraudsters tend to go as far as creating synthetic identities, where they try to create a new identity by combining their real information in conjunction with fake data.
Synthetic fraud is finding fertile ground in new types of consumer financial transactions, especially with peer-to-peer (P2P) payments.
In the first 6 months of 2020, recurring fraud made up 8% of all fraud in the fintech market (see Graph 5).
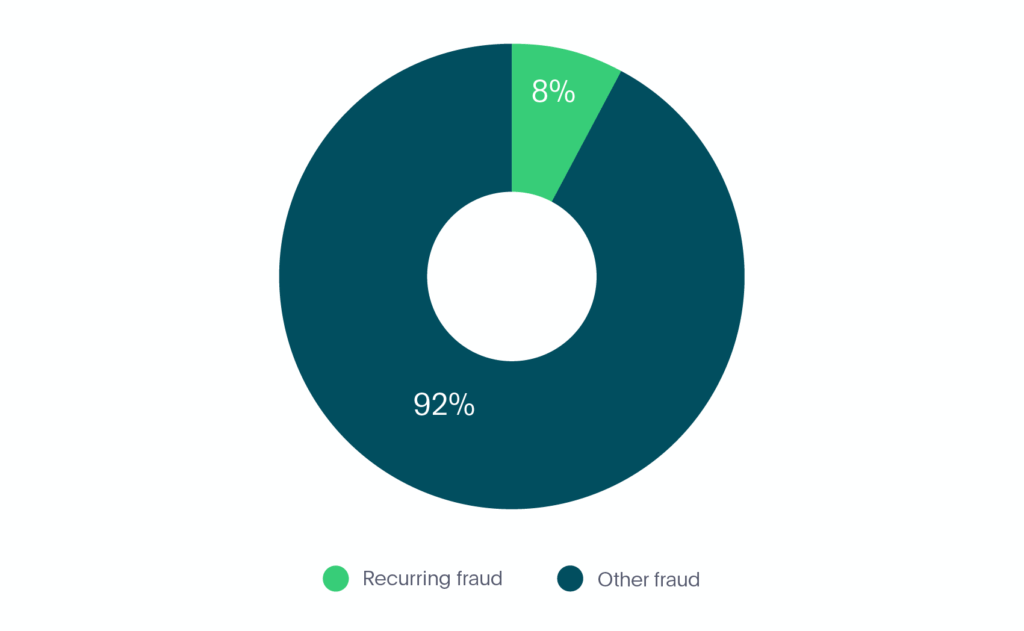
Graph 5. Recurring fraud in fintech
How Veriff fights recurring fraud
Recurring fraud is where our crosslinks shine the brightest. If we’re confident that the end-user has committed fraud before, we’ll automatically decline all the recurring attempts associated with the same person, device or document.
If the same person, document or device have been found approved in the historically submitted sessions, all the recurring attempts will be declined with Velocity/Abuse.
The Overall Breakdown
Now that we’ve looked at the 4 different types of fraud that we’ve seen within the fintech industry, we can see the full breakdown below (see Graph 6):
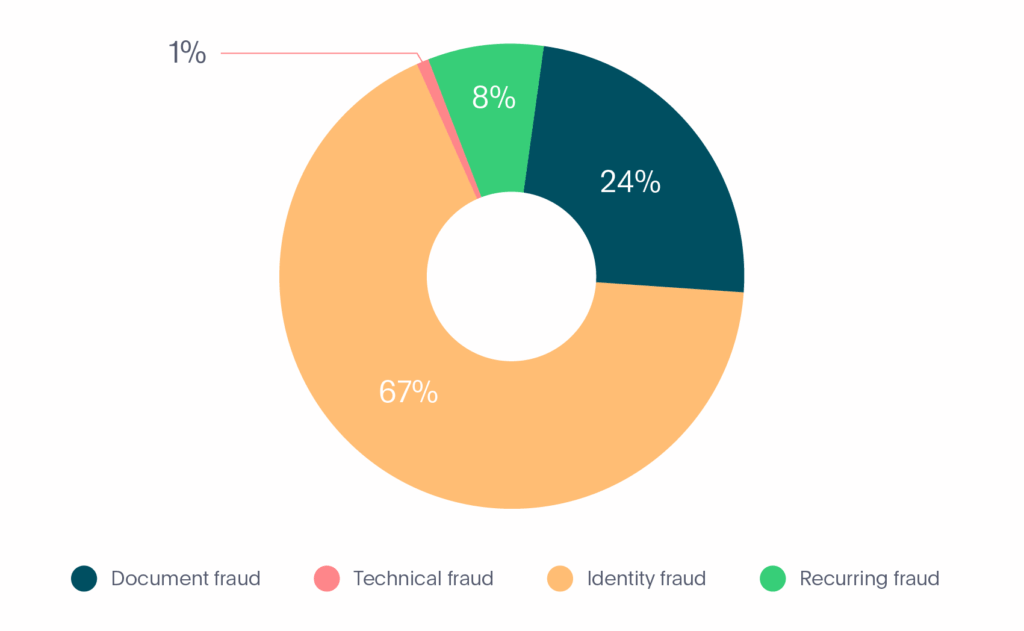
Graph 6. Fraud types in Fintech
- Document fraud – 24%
- Technical fraud – 1%
- Identity fraud – 67%
- Recurring fraud – 8%
Of course in all of the above instances, Veriff is well-placed as a verification provider to fight back against online fraud in all forms. We continue to observe trends across the fintech industry so we can stay ahead of developments, and prevent losses for our fintech partners.
Fintech Innovations
The contributions of the most popular top fintech innovations have been useful in redefining the applications of technology in finance. The most noticeable area for innovation in fintech points to regulatory technology or RegTech. Fintech innovation would find new directions for growth in the domain of regulatory technology. Aside from financial regulators, another innovation is AI. Artificial intelligence would support the future of fintech and companies that want to use the value of intelligent technology. The integration of AI as one of the fintech trends can help in creating sophisticated algorithms that could examine credit profiles within a few seconds.

Talk to us
If you’d like to learn more about Veriff’s fraud prevention technology & gain financial advice, you can visit our website or contact us at sales@veriff.com. And make sure to look out for our next report coming in the near future all about fraud in Mobility.

