IDV Article
Digital Operational Resilience Act (DORA): Key steps for financial services success
As cyber threats grow more sophisticated, protecting financial institutions and their customers has never been more critical. Enter the Digital Operational Resilience Act (DORA), the EU’s game-changing framework designed to fortify the financial sector against digital risks and disruptions.
Introduction
In an increasingly digital world, safeguarding financial entities such as banks, investment firms, and insurers from information and communication technology (ICT)-related incidents is a top priority. DORA aims to enhance the security and resilience of financial systems by requiring most licensed financial entities to implement a comprehensive ICT risk management framework.
In modern finance, technology is the lifeblood that keeps daily transactions flowing. Whether handling online payments, mobile banking, or cross-border transactions, clients expect seamless ICT services and security around the clock. Outages or breaches can damage reputations, destabilize markets, and erode trust. Recognizing these risks, DORA creates a uniform approach to ICT risk oversight and ICT third-party risk management across the EU.
The stakes are high. A single breach or severe disruption can undermine trust in the financial market, jeopardize consumer data, and even pose systemic risks to global stability. Recognizing these challenges, DORA requires financial entities to have a comprehensive ICT risk management framework in place, ensuring they can withstand, respond to, and recover from ICT-related incidents.
Operational resilience is about ensuring continuity. It means having a robust strategy to prevent disruptions, detect vulnerabilities, and mitigate any impact when an event occurs. By imposing stringent requirements on regulated financial entities, EU lawmakers and regulators, through DORA, ensure the financial sector can withstand shocks, recover quickly, and maintain consumer trust, thereby bolstering market stability and protecting the overall economy in today’s interconnected, digital era.
What is DORA?
The Regulation (EU) 2022/2554 known as the Digital Operational Resilience Act (DORA), is a comprehensive legislative framework developed by the European Union. It outlines new regulatory measures to ensure that the financial sector’s ICT infrastructure remains resilient against cyber threats, operational failures, and other ICT disruptions.
It standardizes ICT systems risk management across all EU Member States, removing inconsistencies and aligning supervisory expectations.
DORA applies to a wide range of institutions, including banks, payment service providers, electronic money institutions, investment firms, and insurance and occupational pensions companies. By establishing standardized rules across Member States, DORA eliminates regulatory fragmentation and provides a uniform approach to managing ICT risk.
Oversight is coordinated by the European Banking Authority (EBA), the European Securities and Markets Authority (ESMA), and the European Insurance and Occupational Pensions Authority (EIOPA), which are tasked with issuing technical standards and implementing technical standards to guide compliance.
DORA’s main objectives revolve around harmonizing and reinforcing digital risk management across the European financial sector.
Key aims include:
- Establishing common standards: Create shared protocols for ICT risk assessment, incident reporting, and digital operational resilience testing.
- Improving information sharing: Encourage a culture of transparency where institutions share threat intelligence.
- Increasing accountability: Ensure senior management at financial entities bears responsibility for ICT-related decisions.
- Enhancing oversight: Empower competent authorities like the EBA, ESMA, and EIOPA to supervise the enforcement of DORA and develop implementing technical standards.
Core components of DORA

1. ICT risk management framework
Under DORA, financial institutions must adopt a robust ICT risk management framework capable of detecting, preventing, and responding to cyber threats and other operational disruptions. This framework should be fully integrated into existing governance structures and business processes.
Key requirements include:
- Clear definition of roles and responsibilities for ICT risk oversight.
- Continuous monitoring and timely reporting of ICT-related incidents.
- Regularly updated risk assessments considering emerging threats, such as new malware trends or vulnerabilities in third-party software.
- Periodic reviews of security controls and data protection measures.
A robust strategy isn’t just about meeting regulatory requirements; it’s about creating a culture of security and resilience. Best practices include:
- Frequent training: Ensure all staff, from executive leadership to customer support, understand cyber hygiene and risk management procedures.
- Ongoing monitoring: Implement automated systems to track anomalies and generate alerts.
- Risk prioritization: Allocate resources proportionally to the severity and likelihood of identified risks.
- Board-level involvement: Engage top-level management to prioritize and fund necessary cybersecurity initiatives.
2. Incident reporting
Timely, accurate reporting of incidents is fundamental to limiting damage. DORA mandates that financial entities report any major ICT event—whether a cyberattack, a data breach, or a system failure—to competent authorities within tight deadlines. Specifically, institutions must:
- Provide an initial notification as soon as the incident is detected.
- Submit detailed follow-up reports outlining the root causes, impact, and remedial steps.
- Keep ongoing communication with regulators until the issue is fully resolved.
The sooner ICT-related incidents are reported, the quicker authorities and other stakeholders can coordinate a response. Early reporting allows for faster containment of cyber threats, minimizing data loss and disruption. Additionally, a swift response can help identify patterns or widespread vulnerabilities, benefiting other institutions that might be exposed to similar risks.
3. Operational resilience testing
DORA requires regular digital operational resilience testing to verify that an institution’s ICT framework can withstand attacks and recover quickly. These tests must be comprehensive, covering both internal systems and any critical ICT third-party service providers.
Key guidelines include:
- Frequency: Testing should be periodic, and after any major system upgrade or significant organizational change.
- Documentation: Institutions should maintain clear records of test methods, findings, and remediation efforts.
- Independent assessment: Whenever possible, external experts or specialized internal teams should conduct the tests to ensure impartiality.
DORA encourages entities to use various tests, with threat-led penetration tests taking center stage. These tests simulate real-world attacks to uncover hidden gaps in security measures. Complementary tests include:
- Penetration testing: Simulates real-world attacks to exploit potential security holes.
- Vulnerability assessments: Systematically scan software, hardware, and network infrastructure for known weaknesses.
- Scenario testing: Builds hypothetical scenarios (e.g., a ransomware attack) to evaluate an organization’s emergency response strategies.
4. Third-party risk management
Because many financial entities outsource vital operations to external vendors, ICT third-party risks have grown exponentially. DORA mandates rigorous vetting, contracting, and continuous monitoring of any ICT third-party service providers who handle critical data or systems. This ensures that the resilience efforts of financial organizations are not undermined by unprepared or negligent suppliers.
Beyond selecting and monitoring vendors, institutions must also formalize obligations through clearly defined Service-Level Agreements (SLAs). These SLAs should cover:
- Incident response: Required notification timelines in the event of a breach.
- Data protection: Contractual obligations regarding data confidentiality, integrity, and availability.
- On-site inspections: Rights and processes for audits by the financial entity or competent authorities.
- Liability allocation: Clear delineation of responsibility in case of disruptions or data breaches.
5. Information sharing
DORA promotes a collective defense approach by encouraging institutions to share real-time threat intelligence. Sharing critical information, such as newly discovered malware signatures or phishing scams, enables organizations to anticipate and mitigate risks more effectively. A coordinated intelligence-sharing network can drastically reduce the time between threat discovery and mitigation. By pooling resources and expertise, institutions can more quickly identify emerging threats, patch vulnerabilities, and adapt their defense mechanisms. This collaborative approach also fosters transparency and trust within the broader financial ecosystem.
Impact of DORA on the financial services industry
The most significant impact of DORA is its potential to improve stability and resilience in the financial system. By mandating rigorous ICT risk management frameworks, regular digital operational resilience testing, and swift incident reporting, DORA effectively raises the bar for cybersecurity standards across Europe.
DORA introduces additional layers of oversight and reporting obligations. Financial institutions will have to implement:
- Extended reporting obligations: Firms must promptly notify competent authorities of any serious incidents.
- Ongoing monitoring: Continuous audits and compliance checks to meet or exceed the baseline set by the DORA.
- Closer scrutiny of vendors: The responsibilities for overseeing ICT third-party service providers are more explicit and demanding.
- Alignment of internal processes with technical standards: The European Supervisory Authorities (ESA) will issue technical standards to guide specific DORA-related processes.
While these efforts may be resource-intensive, they help reduce the risk of catastrophic incidents that can lead to reputation damage and huge financial losses.
Implementing DORA can be challenging, particularly for smaller or less digitally mature institutions. Increased need for specialized cybersecurity professionals, overhead costs for maintaining compliance, and the complexity of integrating new regulations into existing risk management frameworks are among the few complexities that financial institutions are or will face. Strategies to address these hurdles include:
- Gradual integration: Implement DORA requirements incrementally, focusing on the most critical gaps first.
- Leverage external expertise: Partner with cybersecurity experts for penetration testing and vendor assessments.
- Automated compliance tools: Use software solutions designed for real-time risk monitoring and reporting.
- Staff training: Regularly upskill employees to remain updated on evolving threats and regulatory changes.
Steps to achieve compliance with DORA
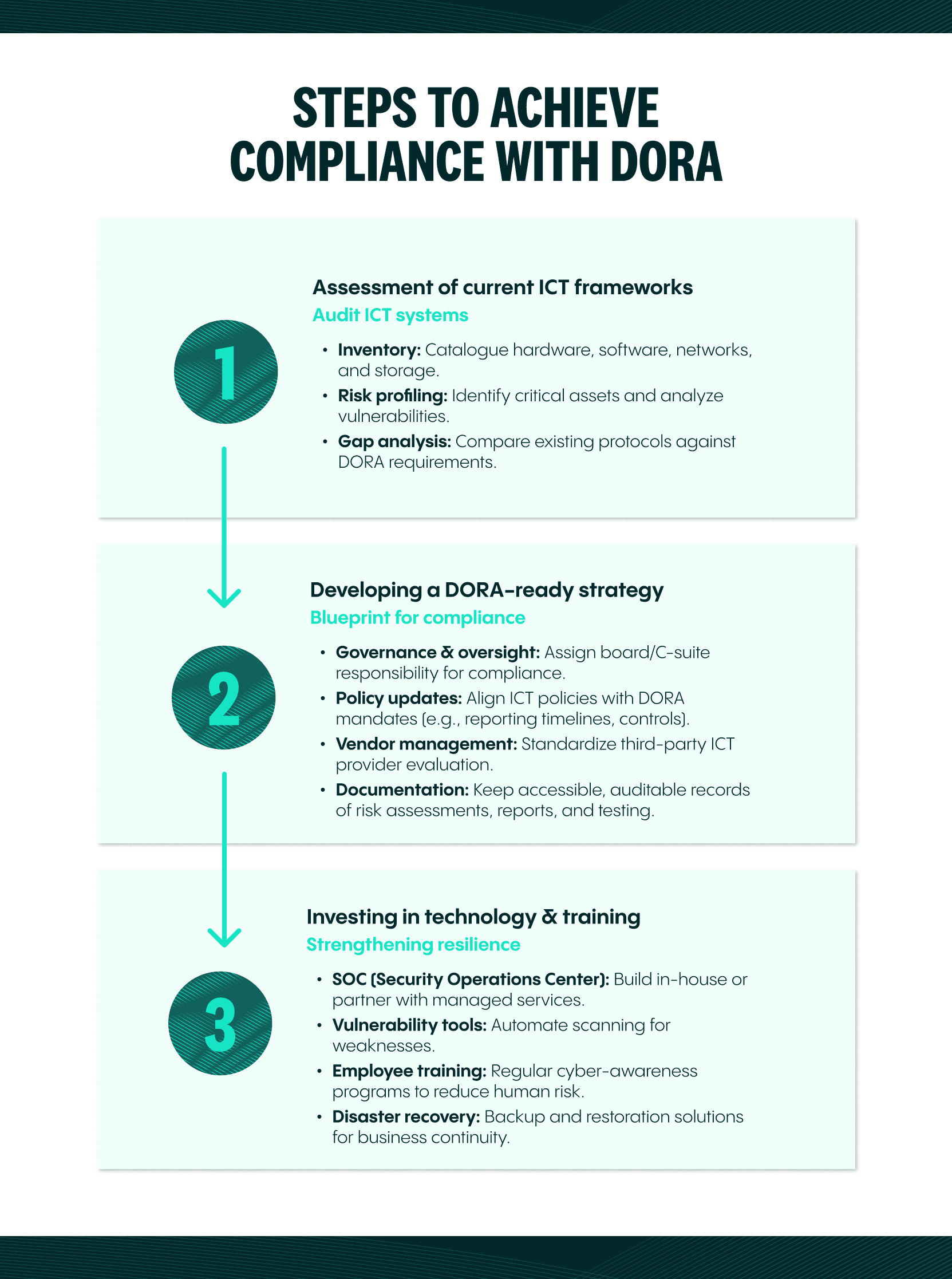
1. Assessment of current ICT Frameworks
The first step is to conduct a thorough audit of your organization’s ICT systems, processes, and policies. This often involves:
- Inventory: Listing all hardware, software, network components, and data storage solutions currently in use.
- Risk profiling: Identifying the most critical assets and analyzing their vulnerabilities.
- Gap analysis: Comparing existing protocols against DORA’s requirements to locate shortcomings.
2. Developing a DORA-ready strategy
Once gaps are identified, institutions can create a roadmap outlining the technical and procedural changes necessary to comply with DORA. Recommended steps include:
- Governance and oversight: Assign specific responsibilities for DORA compliance at the board or C-suite level.
- Policy updates: Revise ICT policies to align with DORA mandates, including incident reporting timelines and security controls.
- Vendor management: Standardize the evaluation process for ICT third-party service providers.
- Documentation: Maintain clear, accessible records of all risk assessments, incident reports, and testing results.
3. Investing in technology and training
Building compliance also means investing in the right technologies and staff training. Essential elements include:
- Security operations center (SOC): Consider forming an in-house SOC or partnering with a managed security service provider to oversee security around the clock.
- Vulnerability assessment tools: Automated scanners can regularly check for known software or network vulnerabilities.
- Conduct threat lead penetration testing: Simulating real-world attacks that would help uncover vulnerabilities.
- Employee awareness programs: Reduce the likelihood of phishing attacks by providing regular cybersecurity training to employees at all levels.
- Disaster recovery solutions: Backup and recovery tools that facilitate quick restoration if an attack or outage occurs.
DORA and the future of financial services
DORA is set to transform how financial entities approach digital innovation. By mandating high security and resilience standards, the regulation ensures that new financial technologies—be they AI-driven investment platforms, mobile banking apps, or crypto assets trading services—are designed with robust safeguards from the start.
DORA is not just a regulatory checkbox—it is a blueprint for embedding resilience into the DNA of Europe’s financial services industry. By enforcing rigorous ICT risk controls and fostering cooperation among EU regulators, the regulation sets a new global benchmark for operational security in the face of evolving cyber threats.

