
IDENTITY & DOCUMENT VERIFICATION

Confirm user identities and documents within six seconds. Prevent fraud, verify every user is real, and build trusted connections with accurate identity verification software that works on a global scale.
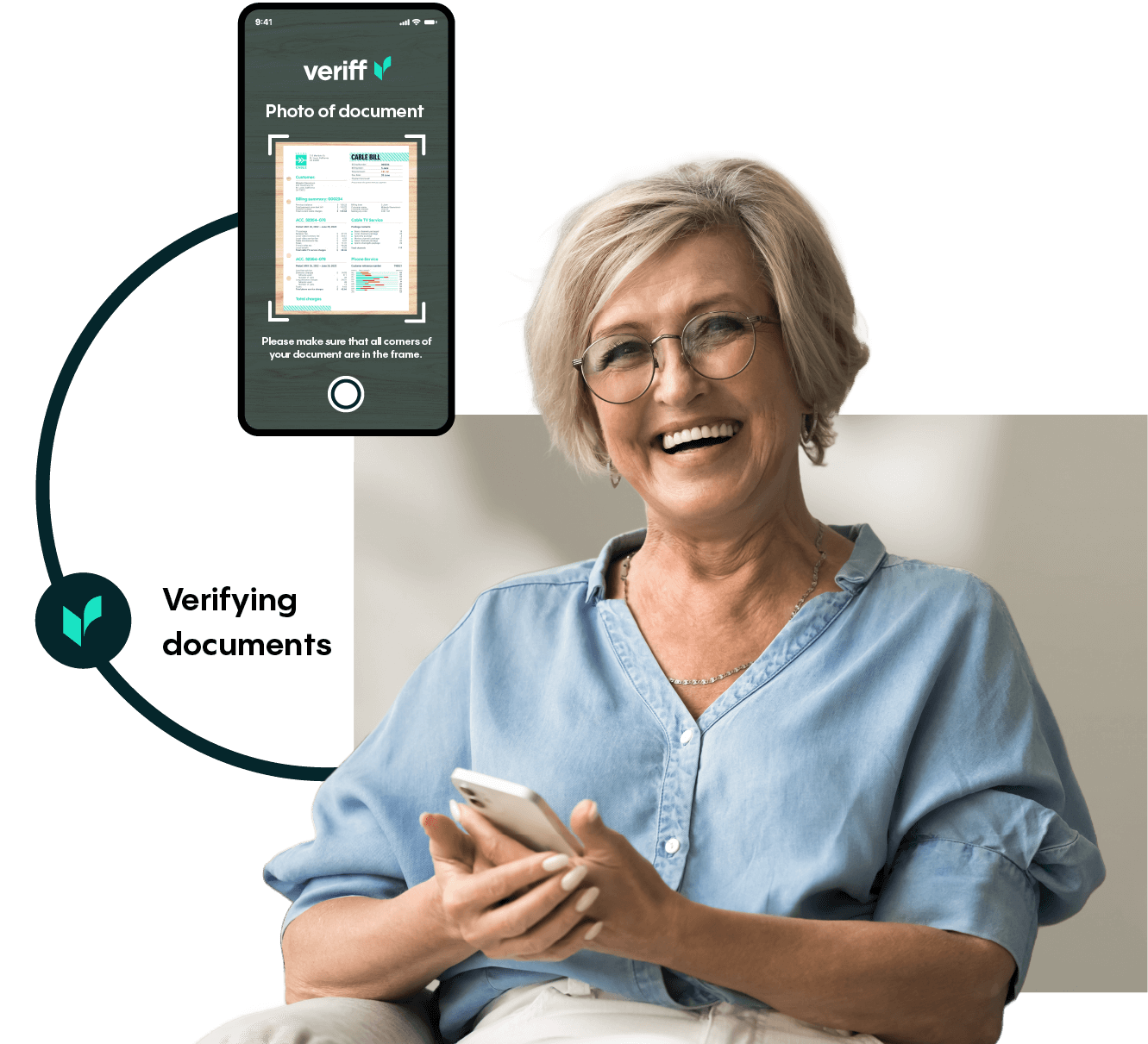
PROOF OF ADDRESS

Confirm proof of address. Veriff’s solution reduces user friction, manual processes, and business risk, while while complying with know your customer (KYC) and customer due diligence (CDD) requirements.

DATABASE VERIFICATION

Cross-reference identities against global databases to strengthen trust, meet regulatory requirements, and catch fraud early with identity verification software that delivers quick and accurate checks.
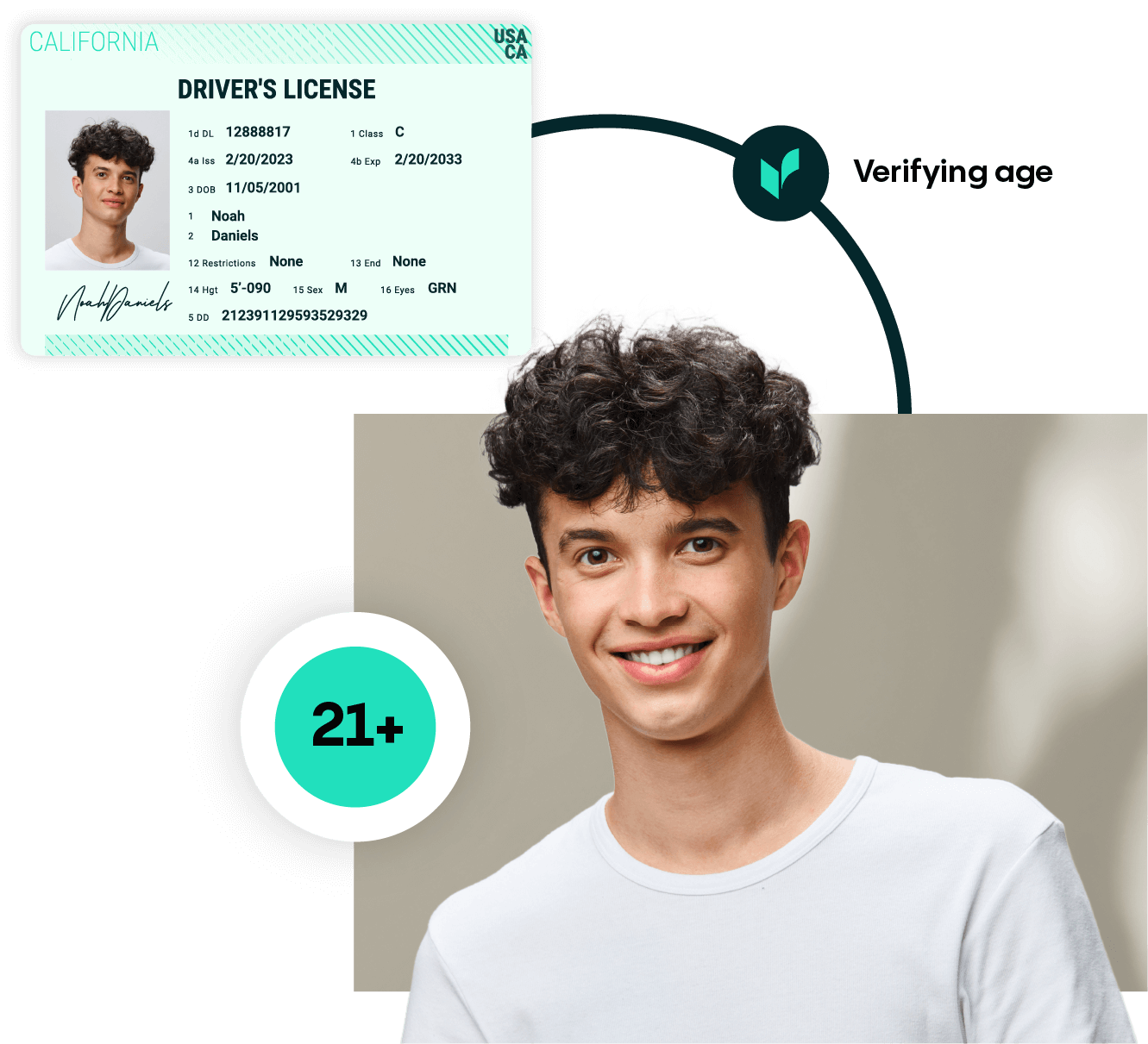
AGE VALIDATION

Automatically verify customer age with AI-driven checks. Prevent underage access with built-in age validation tools that keep your business compliant.

AML SCREENING

Screen individuals against Politically Exposed Persons (PEP), sanctions lists, and adverse media to mitigate risk. Ongoing monitoring helps safeguard businesses while meeting AML and KYC requirements.
Calculate your ROI
Try our ROI calculator to see how Veriff’s trust infrastructure solutions can deliver a strong return while reducing costs.
verified on the first try
second verification
documents supported
languages & dialects

Start building with Veriff for free
Your journey toward faster, more accurate identity verification starts here.
